[ad_1]
Sophos reports that two in three organizations were hit by ransomware attacks in 2021, likely due, in part, to the growing ransomware-as-a-service trade. Understanding what ransomware is and how it works is the first step toward securing your defenses against these attacks
Ransomware is a growing threat in the post-covid era. According to Ivanti’s 2022 Ransomware Spotlight Report, of the 311 known exploits CISA warned federal agencies to address within a specific amount of time, 57 of them (18%) were tied to ransomware. But what makes matters worse is that their research shows that no scanner tools are perfect: only 92.7% of the 288 vulnerabilities they studied that ransomware can exploit were detected by three popular scanners combined.
As such, one of the best ways to prevent ransomware from affecting your business is to better understand this type of threat. We’ve already written at length about ransomware statistics and the ransomware prevention and protection methods you should know. Now, it’s time to break down what ransomware is and answer the question “how does ransomware work?” Our goal is to help you understand what it is and how it operates so you can strengthen your defenses against potential ransomware attacks.
Let’s hash it out.
How Does Ransomware Work? A 30-Second Overview (TL;DR)
The way ransomware works is that an attacker uses a type of malicious software to encrypt your IT systems and/or data. They then hold your sensitive data captive until you agree to pay for access to a decryption key.
Here’s a quick overview of how ransomware works from a step-by-step perspective:
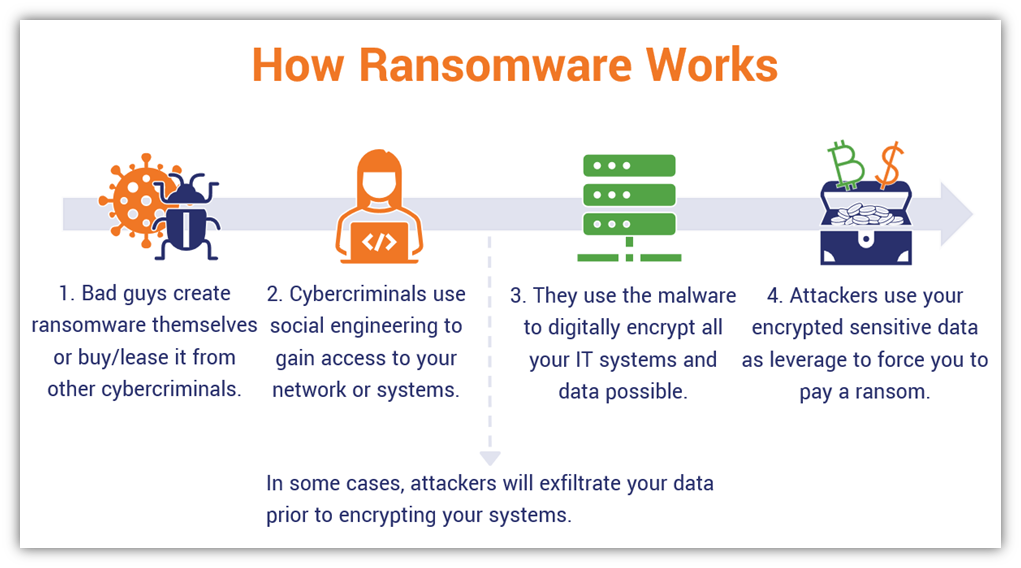
Don’t worry — we’ll go into all of this more in depth in a little bit. But first, there’s something that we think might be helpful for some of you before we get into all that.
A Quick Recap: What Is Ransomware?
Ransomware is malicious application or code that cybercriminals use to restrict access to, alter, destroy or steal your most sensitive data and systems. It typically uses encryption — a method of converting data from a readable format into utter gibberish through the use of a cryptographic key — to restrict your access. They’ll offer a solution — a decryption key that will, essentially, revert that gibberish into readable, useful data — in change for some type of demanded payment (i.e., ransom). This is the primary tool, along with phishing and other attack tactics, used in ransomware attacks.
If you find yourself the victim of a ransomware attack, the assailant will offer you the key, but it typically comes with a steep price tag. For example, during a ransomware attack on the tech company Acer, the REvil ransomware gang demanded $50 million in exchange for access to the company’s encrypted data. And that price tag was just the cost of the ransom itself — it doesn’t include the direct and indirect costs associated with mitigating the attack and dealing with everything that follows (including unanticipated downtime and outages).
No matter how much data you have, cybercriminals want to get their grubby hands on it. This way, they can either use it for nefarious purposes, or sell/trade it to others who will use it for the same.
Virtually Anyone Can Be the Target of a Ransomware Attack
Unless you’re living your life without ever touching a computer or electronic device of some kind, ransomware has the potential to impact you. Contrary to popular belief, ransomware attacks don’t just target major enterprises. The previously mentioned Sophos report shows that mid-size organizations (100-5,000 employees) also make a tempting target for cybercriminals.
This is particularly worrisome considering that this underreported group of 32.5 million businesses represents 99.9% of all U.S. businesses (according to the Small Business Administration [SBA]).
The FBI even reports that private individuals are targeted in ransomware attacks. Data from the Bureau’s Internet Crime Complaint Center (IC3) shows that the agency received 3,729 ransomware complaints with adjusted losses of nearly $50 million in 2021.
Basically, the idea here is that if the bad guys can block you from everything, thereby crippling your business, you’ll feel like you have no choice but to pay whatever they ask to get the decryption key.
Spoiler Alert: Cybercriminals Aren’t Always True to Their Word
While this may come as a surprise to some of you, it’s important to keep this truth in mind when weighing your options about whether to pay a ransom: cybercriminals lie. Even if you bother to pay their exorbitant ransom demands, there’s no guarantee that they’ll follow through with sending you the decryption keys — or, even if they do, that the keys will work as promised.
The FBI IC3’s 2021 Internet Crime Report states that paying a ransom doesn’t guarantee that your files will be recovered. However, it may encourage additional future attacks against your organization and others. If they know you’re willing to pay their demands, then you may be an especially appealing target.
You May Face Civil Penalties For Making Ransomware Payments
There’s also the trouble that if you decide to pay a ransomware demand, you may find yourself facing civil penalties. This can happen if the U.S. government is sanctioning the cybercriminals you’re paying. The U.S. Department of the Treasury reports that the Office of Foreign Assets Control (OFAC) may still be able to impose those penalties based on “strict liability,” meaning that you can still face those penalties even though you “did not know or have reason to know” that the person you’re dealing with faces sanctions under OFAC laws and regulations.
Clearly, ignorance isn’t always bliss.
Not All Threats Come From Outside Your Organization
This may come as a surprise, but some ransomware attacks involve internal threat actors. Data from a 2021 Hitachi ID Systems poll shows that 65% of North American organizations’ IT and security personnel say they were approached directly by cybercriminals to aid in ransomware attacks against their employers. According to Cyberreason, LockBit is one example of a ransomware-as-a-service platform that’s trying to solicit employees into compromising their employers.
But how did attackers try to reach them? Hitachi reports that a whopping 59% of those outreaches came via email — another 27% of communications were received via phone calls and 21% through social media. What makes attackers’ recruitment efforts particularly concerning is that they’re offering 85% of employees either cash transfers or Bitcoin payments worth up to $1 million.
All it takes is one employee accepting such a deal to bring your company to its knees.
How Does Ransomware Work? A Step-by-Step Look at How This Cyber Attack Occurs
In some cases, ransomware attacks are automated attacks that attack companies and individuals randomly. In other cases, they target specific businesses, organizations, and even local, state or federal government entities. Once they choose a target, it’s game on for these schmucks.
Knowing this, it’s time to answer the question “how does ransomware work?”
1. Bad Guys Create Malicious Programs (or Hire a Ransomware Operator to Do It For Them)
If someone has the know-how to create ransomware, they can code the malicious programs to operate however they choose. But in many cases, most attackers don’t have the skill or inclination to create their own malware. Instead, they hire someone with their own malicious software to do their dirty deeds for them by buying or leasing their ransomware capabilities.
This unsavory trade, known as ransomware-as-a-service (RaaS), gives shady individuals (RaaS affiliates) access to ransomware tools (typically in kits) so they don’t have to create the malware programs themselves. These kits often include 24/7 support from the RaaS operators and a variety of other services you’d come to expect from legitimate software-as-a-service providers.
Here’s a quick breakdown of the roles of ransomware operators and the people who hire their services:
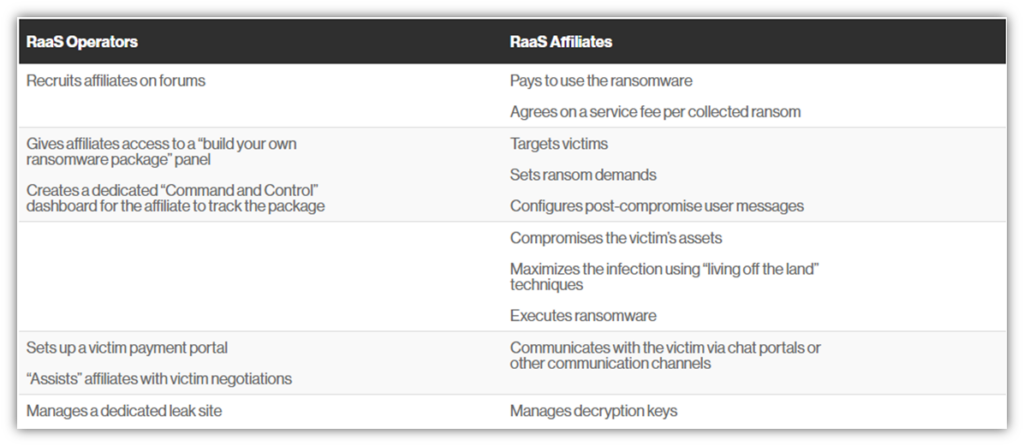
Examples of common RaaS families Sophos observed in 2020-2021 included:
- Conti (16%)
- REvil (15%)
- Ryuk (9%)
- LockBit (4%)
- Ragnarok (4%)
2. They Use Whatever Means to Infiltrate Your Network & IT Systems (i.e., Exploiting Human & Tech Vulnerabilities)
Cybercriminals are always looking for a way into your organization’s IT systems and data. There are a few ways they can gain the desired access:
- Exploit weaknesses in your device’s browser, network, or other IT systems (such as exploiting unpatched or outdated software or plugin security vulnerabilities).
- Carry out phishing attacks to trick or manipulate employees into providing sensitive information or access.
- Target a third party in your supply chain to compromise their access to your systems.
- Use fake, malicious ads to auto install ransomware onto your device, which they can use as a foothold to infect your larger network and access connected systems.
Exploit Unpatched Vulnerabilities & IT Weaknesses
Apple recently found itself making headlines because cybercriminals have been able to exploit vulnerabilities within their operating system after a recent update. One potential concern is that if hackers used one of these exploits to take control of your device, they could use that access to install whatever malware (such as ransomware) they want onto it.
The good news is that Apple released several updates this month (Aug. 17 and 20) to quickly address these vulnerabilities in multiple operating systems.
Use Social Engineering Tactics and Phishing Attacks on Your Employees & Other Network Users
Much like its namesake (fishing), phishing is all about setting bait to lure and reel in an unsuspecting target. Phishing can occur in a lot of ways:
- Tricking employees into opening malicious emails. Cybercriminals love to use email to send malicious attachments and links to dangerous websites.
- Coercing or enticing users into plugging in malicious hardware. Some attackers are known to send tchotchkes, such as free USB storage tokens, to entice you to plug them into your company device. Once connected, the devices can enable attackers to get their ransomware onto your device.
- Tricking users into using remote desktop protocol application. A remote desktop protocol, or RDP, is a way for someone to gain remote access to and control of your device. (More on RDP in a moment)
The Uptime Institute estimates that downtime for nearly 40% of organizations results from human error. A whopping 85% is attributed to employees’ failure to follow organizational processes and procedures.
Capitalize on Insecure Remote Desktop Protocols (RDPs)
Remote desktop protocols are useful tools that enable remote access to a device and are typically used by IT admins. However, when used by people with nefarious intentions, these tools can be used to carry out an assortment of malicious activities (RDP attacks) on your device.
Cybercriminals sometimes use phishing emails — think of common tech support scams — to trick, manipulate, or coerce people into installing the software to get the “tech support” they think they need. According to the FBI, there were 23,903 tech support fraud complaints in 2021 with losses totaling more than $347 million.
Of course, not all RDP attacks involve the use of phishing emails. In some cases, cybercriminals will capitalize on known and zero-day (i.e., unknown or unannounced) vulnerabilities they can exploit to gain access to your systems.
Use Watering Hole Attacks on Websites You’re Known to Frequent
Not all ransomware attacks will target your organization directly. In some cases, cybercriminals have been known to target websites you or your employees are known to visit (such as a third-party vendor’s website). Why? Because they can use an auto installer to get their ransomware onto your device.
3. They Encrypt Your Data and Systems So You Can’t Access Them
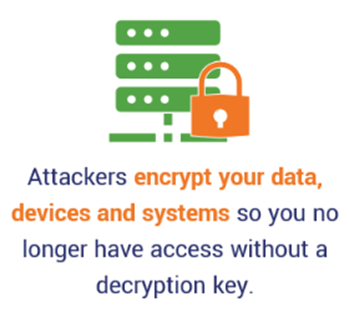
Continuing on with our list of how ransomware works is what bad guys do once they get into your systems: encrypt everything. Simply put, data encryption is the nasty main purpose of ransomware attacks. The idea here is that if an attacker can control access to your sensitive data and resources, they’ve got you where they want you and you’ll feel like you have no choice but to give into their demands.
4. Attackers Demand Beaucoup Bucks in Exchange For Access to Your Data and Systems
Typically, attackers upload basic text files to the encrypted server, directory, or device that communicate who the attackers are and their demands. In some cases, these notes will offer to provide a decryption key and program in exchange for X amount of cryptocurrency (commonly Bitcoin) that must be paid within a specific amount of time.
Of course, not all attacks are always such straightforward transactions. Unfortunately, as some companies and organizations have learned the hard way, some ransomware attackers have more than one trick up their sleeves…
OPTIONAL: Before Encrypting Your Data, Some Attackers Will Exfiltrate Your Data to Servers They Control
In some cases, the “fun” doesn’t stop there. Some bad guys, before they encrypt your systems and data, will exfiltrate (a fancy word for “withdraw” or “steal,” in this case) your sensitive data to a server they control. Why do this? So, they can hit you up for additional money or cause additional damage to your brand and reputation by publishing the information online.
Either way, unauthorized data exfiltration is bad news and will result in damage to your brand and reputation in one way or another.
Take Steps Now to Protect Your Organization Against Future Ransomware Attacks
Now that we know how ransomware works, it’s time quickly talk about what you can do to protect yourself against these types of attacks. We’ve explored this topic at length in the article “11 Ransomware Prevent & Protection Methods to Implement Now” we mentioned earlier. However, we’ll briefly cover a few of the top highlights here:
- Training your employees to increase their cyber awareness and ability to recognize (and respond appropriately to) phishing scams, sites, and tactics
- Securing your network perimeter and any connected devices with the right tools, policies, processes, and procedures
- Implementing effective PKI-based identity and access management
Check out the article for a more in depth look at these suggestions and other methods. But before we wrap things up here, there’s one last important thing we want to mention: be sure to store your data in both online and offline backups. This way, you have a backup to your backup in the event that an attacker manages to get their hands on your online backup. A good recommendation is to follow the 3-2-1 backup rule.
Final Thoughts on How Ransomware Works
Hopefully, this article answers your question “how does ransomware work?” and gives you a lot to think about regarding what you need to do to protect your organization.
As you can imagine, ransomware creates lot of problems for companies and their customers in many ways. In terms of your organization, a ransomware attack can cause operations to come to a screeching halt and result in everything from lost customer trust and damaged relationships to lost revenue and lawsuits.
From your customers’ perspectives, it can cause them to lose trust in your brand and lead them to turn to your competitors for business from now on. Data from a global survey by Axway supports this:
- 75% of consumers would halt business with companies that reported cyber attacks or data breaches that may have exposed their data.
- 51% would not ever engage in business with organizations that previously reported experiencing a cyber attack or data breach.
Knowing this, you need to decide where you want data breach prevention and mitigation to fall on your list of IT security priorities. The time to plan and get your ducks in a row is now. Don’t wait until you’re already under attack to start thinking about how you want to respond when crap hits the fan.
The post What Is Ransomware & How Does Ransomware Work? appeared first on Axnhost.com.
[ad_2]
Article link
